
A new bill worming its way through Congress has drawn ire from free speech and digital privacy advocates. The new bill, introduced in early March and called the Eliminating Abusive and Rampant Neglect of Interactive Technologies (EARN IT) act, could effectively end person-to-person (p2p) encryption on messaging apps. Critics of the bill claim that it is a massive overreach of government authority, and a major threat to the Constitution’s guarantee of free speech and privacy on the internet.
The EARN IT act, full-text available here, introduces new “guidelines” for companies to abide by in order to maintain their protections under Section 230 of the US Legal Code. Although the words “encryption” are never mentioned in the text of the bill, critics claim that the EARN IT act effectively gives government officials the power to force companies to break encryptions on sensitive documents if they do not abide by state-approved “best practices.” The bill was introduced by Senators Lindsey Graham (R-SC) and Richard Blumenthal (D-CT).
Supporters of the bill claim that federal oversight of companies’ data activity is necessary to crack down on sex trafficking and the sexual abuse of minors. The self-cited primary purpose of the bill is: “to prevent, reduce, and respond to the sexual exploitation of children, including the enticement, grooming, sex trafficking, and sexual abuse of children and the proliferation of online child sexual abuse material.” However, critics point out that the bill does not actually target child sexual abuse material (CSAM) or sex trafficking activity and instead could potentially give the judicial branch broad power to regulate the activity of internet platforms and access sensitive information.
Section 230 and Current Internet Liability
The EARN IT act focuses specifically on protections established in Section 230 of the US legal code. Section 230 has historically governed how tech companies deal with liability issues stemming from users on their platforms. According to Section 230, providers of “interactive computer services” are generally not liable for any illegal user-generated content on their platforms. For example, Twitter generally is not legally liable if any user posts illegal content on its platform. The point of Section 230 is to give internet companies the ability to self-regulate their own content without the fear of legal retaliation.

The EARN IT act essentially modifies Section 230 to operate on a conditional basis. If companies that provide internet services are found guilty of falsifying data practice results or otherwise not meeting DOJ-approved standards, they will no longer be entitled to protections under Section 230. The result is that companies could be held legally liable if users posted illegal content. Companies could also be compelled to produce documents verifying their data practices.
Content falling under CASM or sex-work related material is already exempt from protections under Section 230, but the new EARN IT act threatens to remove the automatic liability exemption companies enjoy and instead require them to “earn” those protections by following state-approved guidelines. If a company does not meet the guidelines or is found lying on an application, the Attorney General’s office retains the authority to demand that they “produce any documentary material relevant to such certification for inspection and copying.” That means that the US Attorney General’s office, headed by William Barr, could force companies to produce any material they suspect is related to child sex abuse, including private user-related information.
What Does This Mean for P2P Encryption?
The words “encryption” are never mentioned in the text of the EARN IT act. However, critics maintain that the bill and surrounding government proceedings bear an inherently anti-encryption message. Shortly after the final text of the bill began circulating, the DOJ hosted a press conference explaining its own efforts to curb child sex trafficking and introduced a set of 11 “voluntary principles” that a growing number of tech companies have pledged to follow.
During the conference, Barr expressed that child predators “communicate using virtually unbreakable encryption” and that his department was focused on “addressing child exploitation in our efforts on retaining lawful access and in analyzing the impact of Section 230 of the Communications Decency Act on incentives for platforms to address these crimes.” Barr also added: “Predators’ supposed privacy interests should not outweigh our children’s privacy and security.”

Critics have interpreted the bill in light of the Barr administration’s noted anti-encryption agenda. Barr has been a long-time critic of tech companies’ adherence to end-to-end encryption and has suggested that the technology prevents law enforcement from handling cases of sexual abuse involving minors and domestic threats of terrorism. Barr has previously demanded that Apple unlock users’ phones to gather info on domestic terrorism issues and also co-authored an open letter to Facebook explicitly asking the company to not use p2p encryption on its messaging services.
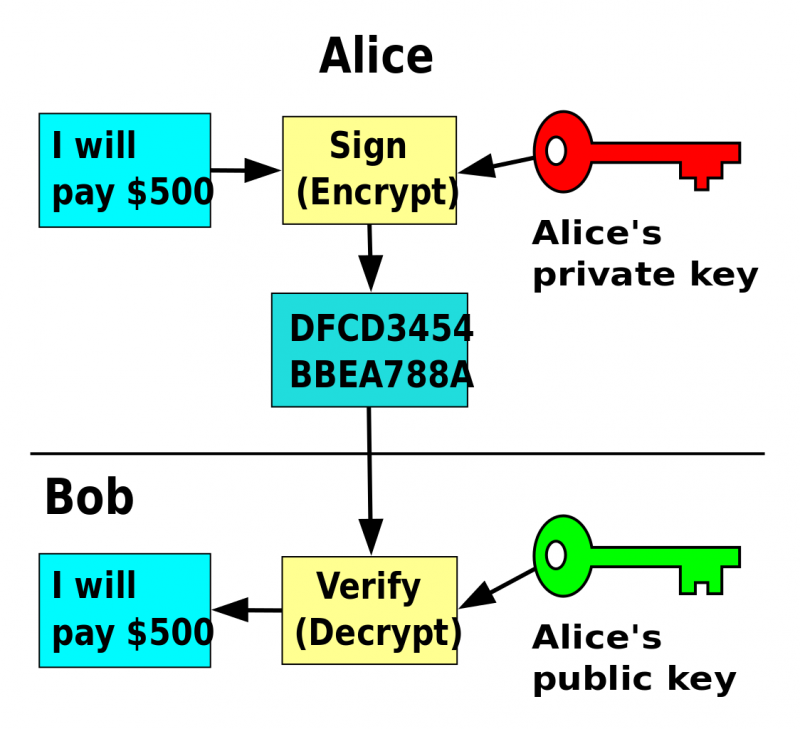
The main worry from p2p encryption advocates is that under the new EARN IT act, internet companies may not be eligible for Section 230 protections if they offer end-to-end encryption services on their platforms. Companies would either be forced to accept liability, stop providing the service, or install a backdoor on encryption protocols for US officials, which would undermine the entire purpose of encryption in the first place.
Further, critics of the new bill have cited President Trump’s eagerness to take on tech companies as a cause for concern. Trump has frequently claimed that tech companies control their platforms to censor conservative speech and other Republican figures have also joined in the fight against encryption. Following a bipartisan panel on encryption for data companies, Judiciary Chairman Lindsey Graham (R-SC) said: “This time next year, if we haven’t found a way that you can live with, we will impose our will on you,”
So even though the EARN IT act has no explicit prescriptions regarding data encryption, it leaves open the possibility that the DOJ could sanction companies that utilize the service on their platform. If the current administration’s previous attitudes regarding encryption are any indication, the EARN IT act could usher in a new era in the battle over digital privacy and freedom of speech in the US.
The current US administration is not alone in its battle against encryption. Both the UK and Australia have passed anti-encryption measures within the past few years, citing security concerns as the main motivation. At the DOJ’s recent press conference, James Brokenshire, security minister of the UK said in regards to end-to-end encryption: “I’ve got to say that putting our children at risk for what I believe are marginal privacy gains is something I really struggle to believe any of us want.”
However, many privacy law experts disagree with Brokenshire’s claim. According to ACLU Senior Legislative Counsel Kate Ruane: “The EARN IT act threatens the safety of activists, domestic violence victims, and millions of others who rely on strong encryption every day. This legislation would empower an unelected commission to effectively mandate what Congress has time and again decided against, while also jeopardizing free expression on the Internet in the process.”
Do We Have a Digital Right to Privacy?
The EARN IT act also raises implications for issues surrounding digital privacy. Although the US Constitution does not explicitly include the right to privacy, the Supreme Court has consistently ruled that the Constitution implicitly grants a right to privacy against government intrusion, the most famous example being the decision in Griswold v. Connecticut.
As more of the world has moved online, new technologies have made it easier than ever for governments and corporations to monitor people’s activity through the web. Many argue that existing privacy laws are not adequate for the digital age. In the US, there is currently no legal standard for what “digital privacy” entails, though several organizations argue that the right to privacy naturally extends to the digital sphere. Just as the right to privacy protects us from government intrusion within our homes, digital privacy protects from government intrusion into the private aspects of our digital lives.
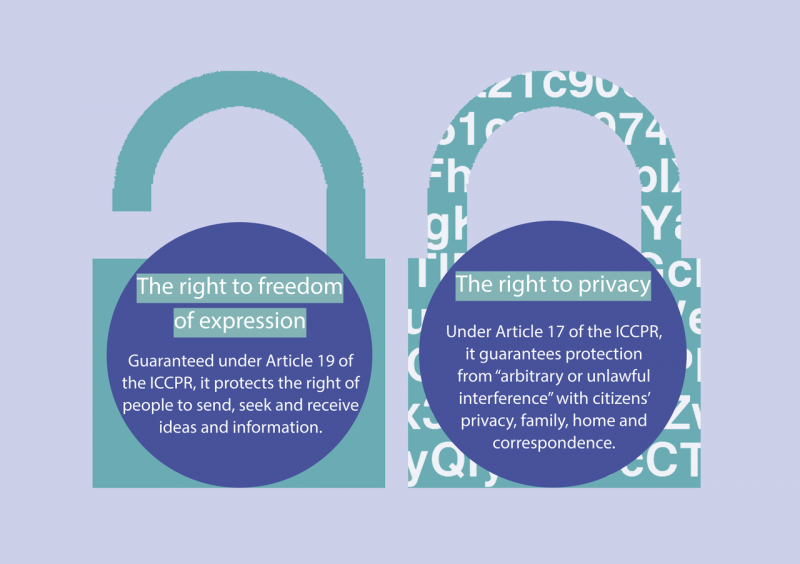
It is clear to see how the EARN IT act could encroach on privacy. It would grant the DOJ the authority to audit internet companies’ user-related materials, including personal data and messaging data. If companies acquiesce to the DOJ’s demands and put backdoors in all of their encryption protocols, then the government could essentially spy on users’ day-to-day communications with no repercussions. Hence why the EARN IT act has tripped the alarm for many internet free speech and anti-surveillance watchdog groups.
The EARN IT act is currently making its rounds through legislative channels and has not been passed into law yet. If it does though. many believe that it will pave the way for virtually unfettered government regulation of internet companies’ editing policies, which is protected under the First Amendment. There are also arguments that it could violate the Fourth Amendment by allowing the government to search and seize people’s personal data without probable cause or a warrant.
Regardless of the outcome, activists are worried about the precedent that the EARN IT act will leave going forward. Some argue that the bill will not pass scrutiny in the House or Senate, but is meant to generate a string of appeals that could reach all the way to the Supreme Court and reverse important decisions regarding privacy.







